AWS Secrets Manager Secret Store
The aws_secrets_manager store enables Spice to read secrets from AWS Secrets Manager by specifying the secret’s name with a selector.
secrets:
from: aws_secrets_manager:my_secret_name
name: aws
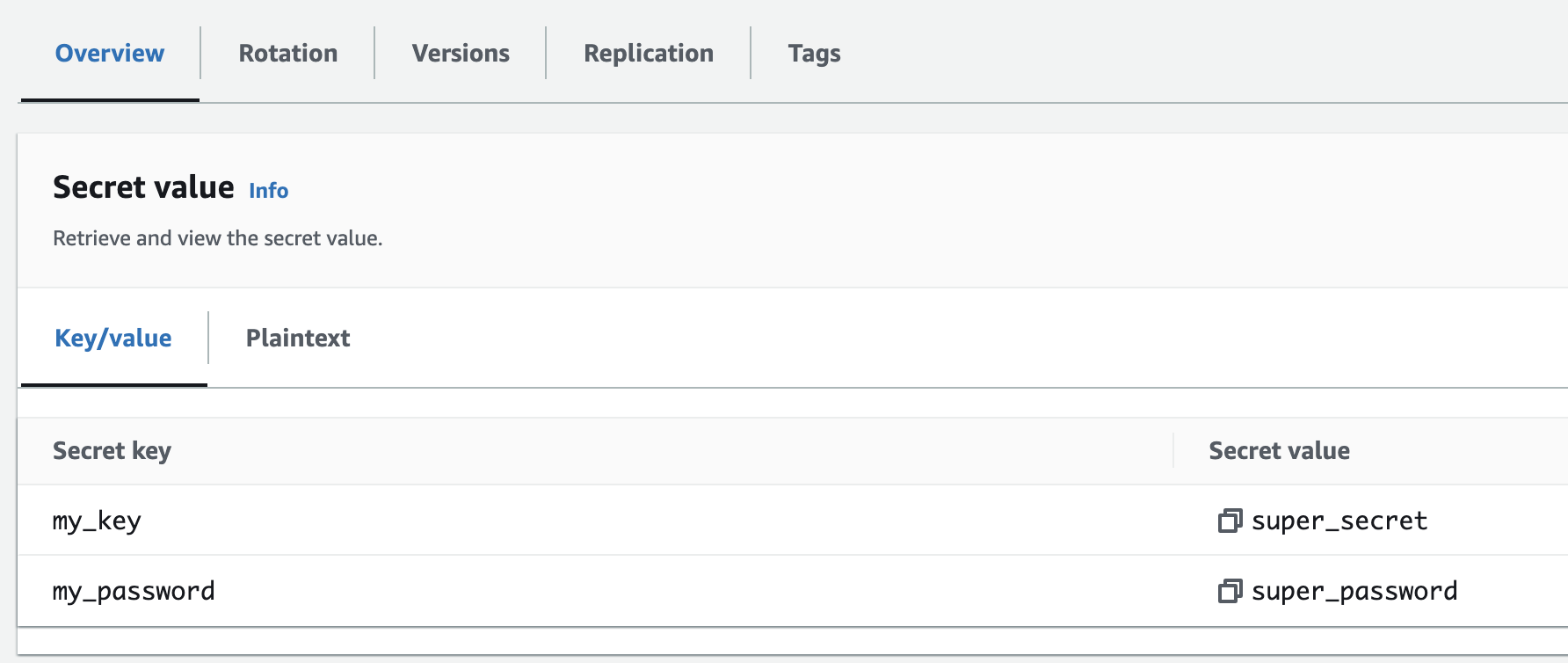
The store reads keys from the secret named in the selector. In the above example my_secret_name must be defined in AWS Secrets Manager, and any keys referenced using ${aws:my_key} will look for a key my_key within my_secret_name.
Example
A complete spicepod definition with a dataset that uses a secret from AWS Secrets Manager.
version: v1
kind: Spicepod
name: taxi_trips
secrets:
- from: aws_secrets_manager:dremio
name: dremio
datasets:
- from: dremio:datasets.taxi_trips
name: taxi_trips
description: dremio taxi trips
params:
dremio_endpoint: grpc://20.163.171.81:32010
dremio_username: ${dremio:username}
dremio_password: ${dremio:password}
Authentication
Spice will automatically load credentials to connect to AWS Secrets Manager from the following sources in order.
-
Environment Variables:
AWS_ACCESS_KEY_IDandAWS_SECRET_ACCESS_KEYAWS_SESSION_TOKEN(if using temporary credentials)
-
Shared AWS Config/Credentials Files:
-
Config file:
~/.aws/config(Linux/Mac) or%UserProfile%\.aws\config(Windows) -
Credentials file:
~/.aws/credentials(Linux/Mac) or%UserProfile%\.aws\credentials(Windows) -
The
AWS_PROFILEenvironment variable can be used to specify a named profile, otherwise the[default]profile is used. -
Supports both static credentials and SSO sessions
-
Example credentials file:
# Static credentials
[default]
aws_access_key_id = YOUR_ACCESS_KEY
aws_secret_access_key = YOUR_SECRET_KEY
# SSO profile
[profile sso-profile]
sso_start_url = https://my-sso-portal.awsapps.com/start
sso_region = us-west-2
sso_account_id = 123456789012
sso_role_name = MyRole
region = us-west-2
tipTo set up SSO authentication:
- Run
aws configure ssoto configure a new SSO profile - Use the profile by setting
AWS_PROFILE=sso-profile - Run
aws sso login --profile sso-profileto start a new SSO session
-
-
AWS STS Web Identity Token Credentials:
- Used primarily with OpenID Connect (OIDC) and OAuth
- Common in Kubernetes environments using IAM roles for service accounts (IRSA)
-
ECS Container Credentials:
- Used when running in Amazon ECS containers
- Automatically uses the task's IAM role
- Retrieved from the ECS credential provider endpoint
- Relies on the environment variable
AWS_CONTAINER_CREDENTIALS_RELATIVE_URIorAWS_CONTAINER_CREDENTIALS_FULL_URIwhich are automatically injected by ECS.
-
AWS EC2 Instance Metadata Service (IMDSv2):
- Used when running on EC2 instances.
- Automatically uses the instance's IAM role.
- Retrieved securely using IMDSv2.
The connector will try each source in order until valid credentials are found. If no valid credentials are found, an authentication error will be returned.
Regardless of the credential source, the IAM role or user must have appropriate secretsmanager permissions (e.g., secretsmanager:GetSecretValue) to access the secrets. If the Spicepod connects to multiple different AWS services, the permissions should cover all of them.
Required IAM Permissions
The IAM role or user needs the following permissions to access secrets in Secrets Manager:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"secretsmanager:GetSecretValue"
],
"Resource": [
"arn:aws:secretsmanager:us-east-1:123456789012:secret:TestEnv/*"
]
}
]
}
Permission Details
| Permission | Purpose |
|---|---|
secretsmanager:GetSecretValue | Required. Allows reading secret values. |
